Describe the Services to be procured
The concept behind Security Colony is that, if a problem is solved in one organization, it makes sense to make the answer readily available to others so they can take steps to protect their businesses from the same threat and can avoid having to waste money working out a solution to a problem that has already been solved elsewhere. There are hundreds of documents that add up to over $20 million in consulting value. It’s all derived from real-world consulting projects, paid for by real organizations. Included in the service are the following components;
- A resource library containing hundreds of security related documents including policies, standards, strategies, presentations, awareness, incident response scenarios and much more.
- A library of video presentations
- A high-level security maturity assessment with relevant recommendations and resources
- A breach monitor service that scours the internet for specific (user defined) information that may flag that a breach has occurred.
- A Vendor Risk assessment tool that reviews the internet facing security status of trading partners based on publicly available information.
- Cyber security related question you need guidance on, can be answered through the "Ask a Consultant" forums on the Security Colony.
Why are these services Unique?
While many of the services can be obtained individually, it is not possible to find all services in one portal. In addition, there are sites that provide some components of the resource library, none have the breadth of documents available that have been used by organizations in operational environments.
Which company is providing the services?
Security Colony Inc
Are these services available from other sources?
We have found no companies that provide the entire suite of services
- SANS has some policy/procedure documents, but they are limited and theoretical
- Advisera - US$999/one off. However, this is ISMS document templates only.
- Gartner has some policy documents but is considerably more expensive than Security Colony
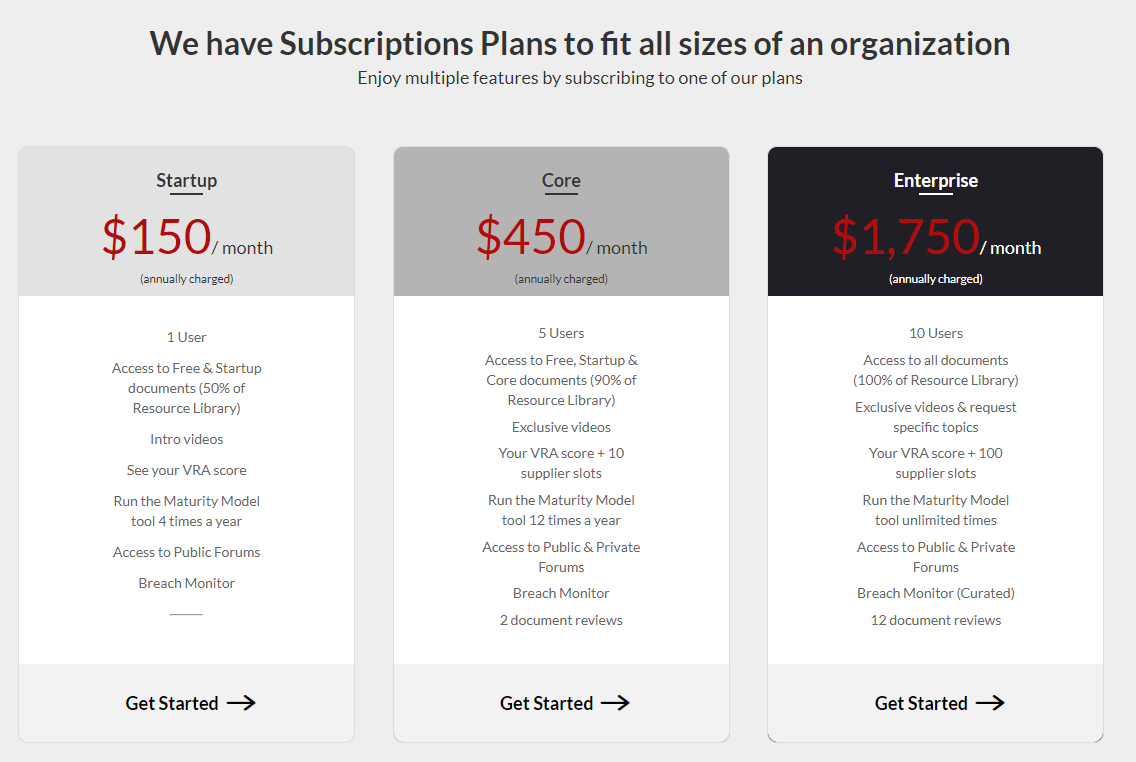
What are the costs of the services?
Is any privacy related information held by the service?
The information held for free subscribers is as follows
- Email Address
- First name
- Last name
The information held for subscribers is;
- Email Address
- First name
- Last name
- Company Name
- Phone Number
What is the term of the service?
The subscription period is 12 months and the subscription will automatically renew at the end of the 12 month subscription period.
Subscribers using a credit card, will receive an email a few days before the next renewal date to notify that the subscription will soon be renewed.
Subscriptions using the 'pay by invoice' option, will receive an email a month before the subscription is due to expire. An additional email is sent a week before the subscription is due to expire with a new invoice for the next year's subscription.
Why are these services essential to our organization?
Developing and maintaining security related documentation and strategies is a labor-intensive activity that requires a range of skills and expertise across many aspects of the security landscape. Our organization does not have the required breadth of experience or the financial and human resources available to effectively improve our documentation and strategy. The scarce resources we have need to concentrate on the 20% of security requirements we have that are unique to our organization. In addition, the service allows us to monitor the internet for data leakages as well as understanding the internet facing security standing of our trading partners.
What is the impact of not subscribing the service?
Not subscribing would mean that we would have to build our security environment from the ground up with the existing resources we possess, or we would need to hire consultants who could help us on our continuous improvement path. In both cases, the process would take longer and cost more than it would if we were able to subscribe to Security Colony.
Does the service pose a security threat to our organization?
The Security Colony platform is designed for users to primarily be ‘consumers’ of the information on the platform which is uploaded/managed by Trustwave. Information considered sensitive is encrypted (or hashed) at rest. This includes contents of the Maturity Model (which is encrypted), and password information (hashed). The site is hosted in Canada and penetration tests are completed multiple times per year. As a security firm, Security Colony takes the security of the site very seriously and strives to ensure that users of the site are not exposed to any security issues through using the portal.