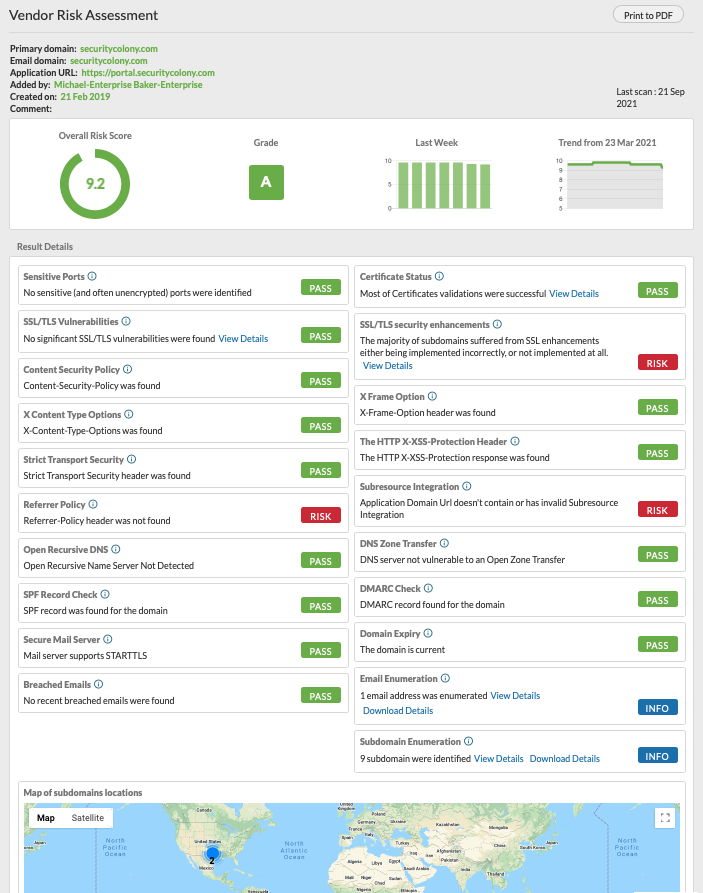
The platform performs a range of checks which are then used to display a final analysis in an easy to use interface.
There are three broad assessment categories which these checks fall into:
(1) Assessing security misconfigurations and vulnerabilities related to server configuration, including:
- Whether an organisation has a strong process for correctly configuring all their encryption (SSL/TLS) certificates
- Whether an organisation has insecure (ie. unencrypted) ports open to the Internet
- DNS server configuration
(2) Assessing security misconfigurations and vulnerabilities related to e-mail system configuration, including:
- Whether an organisation uses strong email security technology (SPF and DMARC)
- Whether employees of an organization have used their corporate email addresses on external accounts, and whether they have then been the subject of a data breach
(3) Assessing security misconfigurations and vulnerabilities related to critical web applications, including:
- A range of security header checks.
Screenshot of the interface is provided below:
The full set of assessments, and corresponding recommendations are:
|
Check Name |
Check Detail |
Recommendation |
|
Sensitive Ports |
This check determines whether your Primary Domain exposes any potentially sensitive services such as administrative interfaces or database endpoints. Exposure of such interfaces to the public Internet increases the likelihood of compromise by malicious parties, and is typically the result of service or firewall misconfiguration. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you review whether there is need to expose these interfaces to the Internet and shut them down where possible. |
|
Certificate Status |
This check determines whether there are any issues with the SSL certificates used to identify services exposed by hosts on your identified subdomains. Some of these issues could potentially be used by a sufficiently resourced attacker to impersonate these services. The check identifies the presence of issues related to key lengths, certificate chaining, timestamps and revocation status. Details on the handling of these, is provided at https://help.securitycolony.com/help/what-do-the-ssl-slash-tls-checks-cover |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you resolve the identified issues by re-issuing secure certificates as appropriate. |
|
SSL/TLS Vulnerabilities |
This check determines whether any services exposed on identified subdomains are using SSL/TLS libraries with known vulnerabilities, potentially exposing service traffic to interception or manipulation by an appropriately placed attacker. These vulnerabilities range in severity from the severe (Heartbleed) to the common (BREACH). Details on the handling of these, is provided at https://help.securitycolony.com/help/what-do-the-ssl-slash-tls-checks-cover |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you reconfigure or update SSL/TLS as appropriate to address the identified vulnerabilities. |
|
SSL/TLS security enhancements |
This check determines whether services exposed by hosts on your identified subdomains implement additional SSL/TLS protective measures that further improve the security of service traffic. Details on the handling of these, is provided at https://help.securitycolony.com/help/what-do-the-ssl-slash-tls-checks-cover |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you consider implementing these additional protections where possible to further improve the resilience of service traffic to interception or tampering attempts. |
|
Content Security Policy |
Content Security Policy (CSP) prevents loading of injected third party scripts in the web browser. Without this control, in the event the application is vulnerable to cross-site scripting attacks, the browser may unknowingly allow execution of injected third-party scripts. |
If this check is marked as 'RISK', we recommend that you implement an HTTP Content Security Policy header. |
|
X Frame Option |
Framing Protection Controls define whether or not a particular page is allowed to be rendered within a frame tag. As framing is allowed by default, an insufficient framing policy makes it possible to embed an affected application within an untrusted third party domain. |
If this check is marked as 'RISK', we recommend that you implement an X Frame Options header. |
|
X Content Type Options |
Content Type Protection prevents certain web browsers from being tricked into loading application responses in an unintended format. Without a Content Types Option header, a browser may be tricked into loading the application in an unintended and unauthorized format resulting in execution of malicious software within the context of the user’s browser. |
If this check is marked as 'RISK', we recommend that you implement an X Content Type Options header. |
|
The HTTP X-XSS-Protection Header |
Cross-site Scripting (XSS) Protection enables the built-in controls preventing against Cross-site Scripting attacks available in certain web browsers. Without this control, in the event the application is vulnerable to cross-site scripting attacks, the browser may unknowingly allow execution of injected third-party scripts. |
If this check is marked as 'RISK', we recommend that you implement an HTTP X-XSS-Protection header. |
|
Strict Transport Security |
HTTP Strict Transport Security (HSTS) policy informs a browser to only send communications over HTTPS. In the event that an application is vulnerable to HTTPS downgrade attacks, the lack of an HSTS header may result in a browser sending unencrypted communications over HTTP, resulting in unintended disclosure of sensitive communications. |
If this check is marked as 'RISK', we recommend that you implement an HTTP Strict Transport Security (HSTS) header. |
|
Subdomain TLS Configuration Consistency |
The public web servers are profiled based on Transport Layer Security configuration, and this profile generates a fingerprint. When reviewing the TLS setup in the subdomains, if a large set of differences are found, it is considered an indicator of application and TLS misconfiguration. The “fail” score is given, depending on the number of differences found. With 100 or less, 2 differences cause a “fail”. Under 1,000 4 sets of differences “fail” |
If this check is marked as a risk, a review of the TLS configurations of servers hosting the listed subdomains is recommended. |
|
Suspicious & Malicious Subdomains |
Subdomain fingerprints are compared to known malicious server lists. If a similarity is detected the subdomain is considered a high indication of a compromise, This assessment uses Transport Layer Security (TLS) server fingerprinting using JARM. |
A “RISK” against this test is a significant issue and we recommend a review of the subdomains in the environment. |
|
Sub-resource Integration |
This check determines whether the Application Domain URL has Sub-resource Integrity (SRI) enabled. SRI is a security feature that enables browsers to verify that resources they fetch are delivered without unexpected manipulation. It works by allowing you to provide a cryptographic hash that a fetched resource must match |
Using Content Delivery Networks (CDNs) to host files such as scripts and stylesheets that are shared among multiple sites can improve site performance and conserve bandwidth. However, using CDNs also comes with a risk, in that if an attacker gains control of a CDN, the attacker can inject arbitrary malicious content into files on the CDN (or replace the files completely) and thus can also potentially attack all sites that fetch files from that CDN. Subresource Integrity enables you to mitigate some risks of attacks such as this. |
|
Referrer Policy |
The Referrer Policy instructs the browser when a ‘Referrer’ header should be sent and what information the header should include. The lack of Referrer Policy may result in unintended disclosure of sensitive information contained within a URL. |
If this check is marked as 'RISK', we recommend that you implement an HTTP Referrer Policy header. |
|
DNS Zone Transfer |
This check determines whether the nameservers for your Primary Domain support zone transfers. A zone transfer is a transfer of all records for your domain, which could potentially leak information about your internal and external infrastructure that would be useful to an attacker. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you disable or restrict zone transfers for your domain. |
|
Open Recursive DNS |
This check determines whether the nameservers for your Primary Domain permit recursive DNS lookups for anyone on the Internet. This kind of DNS query can be used in a "DNS amplification" denial of service attacks by malicious actors. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you disable or restrict zone transfers for your domain. |
|
DMARC Check |
This check determines whether a DMARC record has been defined for your Email Domain (or Primary Domain if an Email Domain was not provided). The DMARC policy published in this record can be used to prevent attackers from forging emails for your organization. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you define a DMARC policy for your domain. |
|
SPF Record Check |
This check determines whether there is an SPF record defined for your Email Domain (or Primary Domain if an Email Domain was not provided). A "Sender Policy Framework" (SPF) record defines which mail servers are permitted to send email on behalf of your domain, which serves to protect you from spammers attempting to imitate your domain. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you implement an SPF record for the domain. |
|
Domain Expiry |
This check determines whether any of the domains you have provided are expired. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you renew your domain registry. |
|
Secure Mail Server |
This check determines whether mail servers for your Email Domain (or Primary Domain if an Email Domain was not provided) support the use of SSL/TLS encryption for email traffic. The lack of support for email traffic encryption increase the risk of attackers being able to read and modify email traffic for the domain. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you enable the use of SSL/TLS for email traffic. |
|
Email Enumeration |
This check determines whether any email addresses for your Email Domain (or Primary Domain if an Email Domain was not provided) are listed by the hunter.io service. Email addresses easily discovered in this manner could be used for phishing attacks against your organization. |
This issue is not itself a risk; however if the findings here are a concern, then we recommend that you provide additional phishing awareness training to your employees. |
|
Breached Emails |
This check determines whether your Email Domain (or Primary Domain if an Email Domain was not provided) are listed have been included in data breaches. Credentials used on other websites could potentially be valid for your environment due to password reuse by end-users, and could potentially be used by a malicious party to compromise your systems. |
If this check is marked as ‘RISK’ and this is your domain, we recommend that you review which email addresses or users were exposed in this manner, and consider forcing password resets for these users. |
|
Subdomain Enumeration |
Subdomains could potentially point to vulnerable systems that are not intended to be accessed, but are nonetheless discoverable. |
This issue is not itself a risk; however if the findings here are a concern, then we recommend that you review the discovered subdomains to ensure that nothing sensitive is being exposed.” Additional information is provided to help analyse these subdomains, the date the subdomain was last detected, the IP address and if this subdomain shares a wildcard DNS - all this is available in the downloadable subdomain listing |
|
Map of subdomain locations |
This map provides the physical locations of all identified subdomain servers, based on geo-location information. |
This issue is not itself a risk; however if servers appear to exist in countries where you aren't expecting them, this is worth investigating. |